.png)


Governance
Home > Services > Governance

Governance
We offer IT governance as a service, providing our clients with the necessary tools and expertise to establish and maintain effective management and control of their IT systems, ensuring compliance with industry standards and regulations, and aligning IT with overall business objectives.
Our Team members are ISO27001 certified and have the skills and acumen to assist your organisation reach certified status.
ISO 27001 is a standard for information security management. It was developed by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC). The standard specifies a set of requirements for establishing, implementing, maintaining, and continually improving an organization's information security management system (ISMS).
An ISMS is a framework of policies and procedures that includes all legal, physical, and technical controls involved in an organization's information risk management processes. The goal of an ISMS is to protect the confidentiality, integrity, and availability of an organization's information assets.
To be certified as compliant with ISO 27001, an organization must demonstrate that it has implemented the required controls and processes specified in the standard. This can be done through an audit process conducted by an external certification body. Once certified, the organization must undergo periodic re-assessment to maintain its compliance with the standard.
ISO/IEC 27001:2013 (ISO 27001) is the international standard that describes best practice for an ISMS (information security management system).
ISO 27001 demonstrates that your company is following information security best practice, and delivers an independent, expert assessment of whether your data is adequately protected. ISO 27001 is supported by its code of practice for information security management, ISO/IEC 27002:2013.
An ISMS is a system of processes, documents, technology and people that helps to manage, monitor, audit and improve your organization’s information security. It helps you manage all your security practices in one place, consistently and cost-effectively.
An ISO 27001-compliant ISMS relies on regular risk assessments, so you will be able to identify and treat security threats according to your organization’s risk appetite and tolerance.
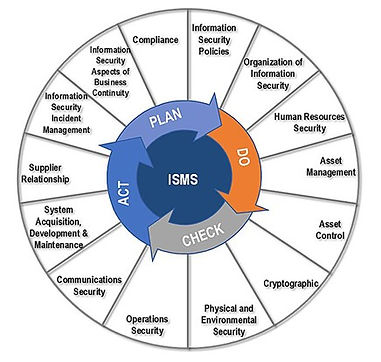
Figure 1: ISO 27001 ISMS
PDCA (plan-do-check-act, sometimes seen as plan-do-check-adjust) is a repetitive four-stage model for continuous improvement (CI) in business process management.
-
Plan: Define the problem to be addressed, collect relevant data, and ascertain the problem's root cause.
-
Do: Develop and implement a solution; decide upon a measurement to gauge its effectiveness.
-
Check: Confirm the results through before-and-after data comparison.
-
Act: Document the results, inform others about process changes, and make recommendations for the problem to be addressed in the next PDCA cycle.

Figure 2: ISO 27001 ANNEXURE A
Annex A of ISO 27001 is probably the most famous annex of all the ISO standards – this is because it provides an essential tool for managing security: a list of security controls (or safeguards) that are to be used to improve security of information assets.
-
A.5 Information security policies – controls on how the policies are written and reviewed.
-
A.6 Organization of information security – controls on how the responsibilities are assigned; also includes the controls for mobile devices and teleworking.
-
A.7 Human resources security – controls prior to employment, during, and after the employment.
-
A.8 Asset management – controls related to inventory of assets and acceptable use, also for information classification and media handling.
-
A.9 Access control – controls for Access control policy, user access management, system and application access control, and user responsibilities.
-
A.10 Cryptography – controls related to encryption and key management.
-
A.11 Physical and environmental security – controls defining secure areas, entry controls, protection against threats, equipment security, secure disposal, clear desk and clear screen policy, etc.
-
A.12 Operational security – lots of controls related to management of IT production: change management, capacity management, malware, backup, logging, monitoring, installation, vulnerabilities, etc.
-
A.13 Communications security – controls related to network security, segregation, network services, transfer of information, messaging, etc.
-
A.14 System acquisition, development and maintenance – controls defining security requirements and security in development and support processes.
-
A.15 Supplier relationships – controls on what to include in agreements, and how to monitor the suppliers.
-
A.16 Information security incident management – controls for reporting events and weaknesses, defining responsibilities, response procedures, and collection of evidence.
-
A.17 Information security aspects of business continuity management – controls requiring the planning of business continuity, procedures, verification and reviewing, and ICT redundancy.
-
A.18 Compliance – controls requiring the identification of applicable laws and regulations, intellectual property protection, personal data protection, and reviews of information security.
The best way to understand Annex A is to think of it as a catalogue of security controls you can select from – out of the 114 controls that are listed in Annex A, you can choose the ones that are applicable to your company.
Please note that not all of these 114 controls are mandatory – a company can choose for itself which controls it finds applicable and then it must implement them (in most cases, at least 90% of the controls are applicable); the rest are declared to be non-applicable. For example, control A.14.2.7 Outsourced development can be marked as non-applicable if a company does not outsource the development of software.

Figure 3: ISO 27001 KEY BENEFITS
One of the major drivers for organisations to work towards certification is that the standard provides an internationally recognised, externally assured, quality mark for Information Security Management. ISO 27001 is the industry yard stick that most Information Security Management activity is measured against.
External assurance is provided to both the customer and the organisation’s management on the actual state of the organisation’s Information Security Management System. External, qualified ISO 27001:2013 auditors impartially review and assess the organisation’s Information Security Practices, policy procedures and their operation against the standard.
This provides a clear, unbiased, scientific view of the actual state of the present Information Security Practices.